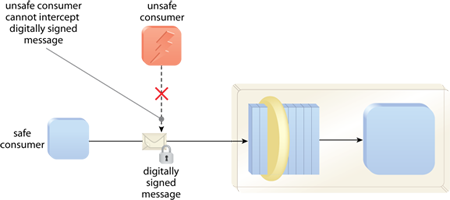
Adaptive Security in Dynamic Group Communications: Dynamics-aware key management and data origin authentication techniques for highly dynamic and large scale multi-party communications: 9783639203745: Computer Science Books @ Amazon.com
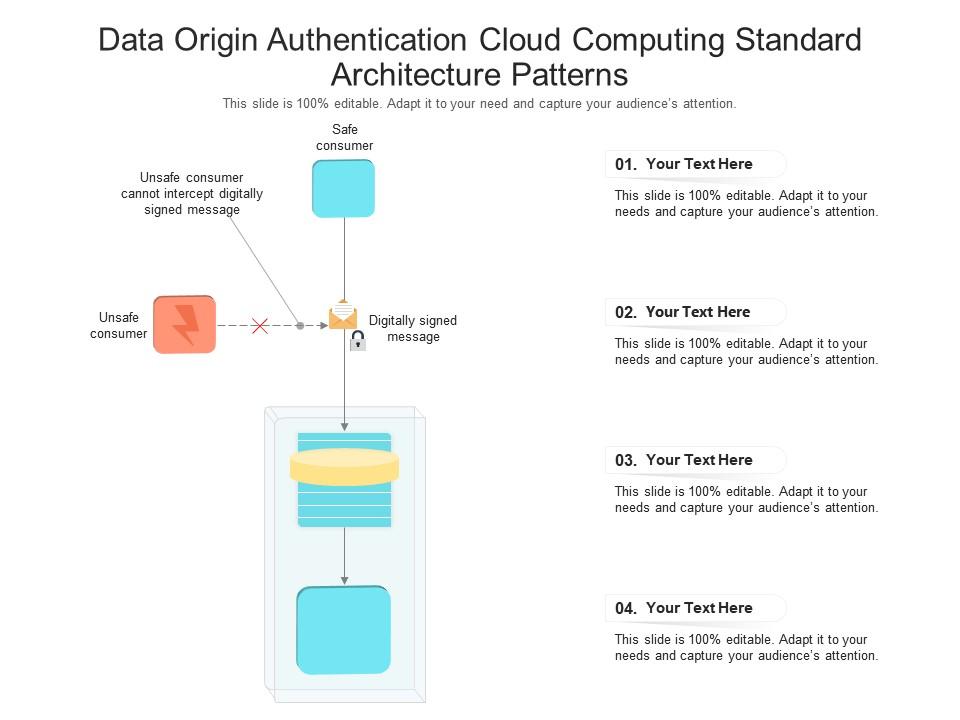
Data Origin Authentication Cloud Computing Standard Architecture Patterns Ppt Presentation Diagram | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

SMUCSE 5349/73491 Authentication Protocols. SMUCSE 5349/73492 The Premise How do we use perfect cryptographic mechanisms (signatures, public-key and symmetric. - ppt download